
The Cybersecurity and Infrastructure Security Agency (CISA) recently announced that single-factor authentication – username and password – is now officially added to their catalog of bad practices – putting it to the list of things that actually help cyberattacks.
To counter cyberattacks, a much better practice is to adopt multi-factor authentication, or MFA. This means the deployment of least two of the following three:
- something you have (e.g. a device)
- something you are (biometrics)
- something you know (e.g. a password)
2004 all over again
And there’s some news on the last one. Last month Microsoft declared the end of passwords across all their consumer accounts.
Already a reality for their business users (including Easy Dynamics!), it is now also the consumer who can ditch their passwords and instead sign in using their Microsoft Authenticator app, Windows Hello, a security key, or an SMS / email verification code.
It’s not the first time that the death of passwords has been announced.
In fact, already in 2004, it was Bill Gates who stated that traditional password-based security was headed for extinction, as it couldn’t “meet the challenge” of keeping critical information secure.
Mr. Gates was quite right there, as since 2004 password vulnerabilities have only become more severe. The latest Verizon Data Breach Investigations Report shows that phishing attacks targeting credentials remain one of the top attack vectors. In fact, compromised passwords were a key element of the SolarWinds attack and MFA would have thwarted at least part of the attack.
So what does the death of the password mean for government agencies?
Well, for starters, that they need to implement MFA. The Executive Order on Cybersecurity from last May give agencies 180 days to adopt MFA, meaning a rapidly approaching deadline of November.
But the second and more important takeaway for agencies is that the end of passwords is an excellent opportunity to boost their cybersecurity, both for their internal as well as their external users.
And while MFA is always better than single-factor, not all MFA is created equal. For instance the “one time password (OTP)” over SMS has proven to be vulnerable for interception and phishing.
Therefore in its recent Draft Federal Zero Trust Strategy , OMB highlights phishing-resistant approaches to MFA and points to the World Wide Web Consortium (W3C)’s open “Web Authentication” standard.
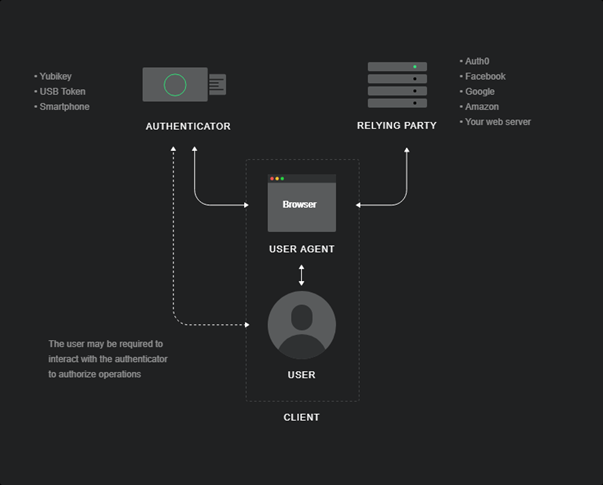
Leaning into the death passwords, and start leveraging secure authenticators such as Yubikeys, USB tokens and fingerprint scanners on smartphones, would significantly help government agencies boost their cybersecurity posture.
Author
-

JJ Harkema is a Senior Manager with Easy Dynamics, working with Federal clients on improving service delivery and digital identity services. Prior to Easy Dynamics, JJ worked at First Data and Experian, and served as a Director at Kantara Initiative. JJ has a M.A. in History and an M.Sc. in Public Management.
View all posts